3. TO-BE
3.1 Overview of possible solutions
Now that we know, what the main issues in identity and data matching are, and what problems should and could be tackled together in the region, we conducted 10 preliminary solutions what were presented in a live workshop on 12th and 13th September in Tallinn. These solutions were described on high level through story telling method involving personas, epic, user stories and use cases. In the following chapter high level description are presented outlining their strengths and weaknesses.
Process and thought behind 3 types of personas
We brought in 3 scenarios based on main persona:
- Willing to cooperate, active person. With scenario 1 we may assume that we are living in an abundance of information if such information exists or can be created. A person is willing to share information necessary to make decision on the identity matching and is also assumed to be active in sharing that information. In this scenario the risk of NOT matching is leaving a person without their right to access the data about them and exercising their rights on that data.
- Unwilling to cooperate, passive and resisting person. In scenario 2 we imagined an actor who does not actively want to connect identities one has in different countries. This may be for simple privacy concerns one has or that such matching would harm a person’s ability to perform intended actions now or in the future. Therefore, the identity matching decision might need to be made in lack of data. User intent on not cooperating may be not detected and even if detected the motivation will not be clear. The biggest risk in this scenario is NOT matching person to existing records and giving them unearned clean start.
- State who is interested to have up to date records in their registries (population registry, social benefits applicants, tax declarations, etc.). The third scenario is meant to allow Member States to perform their duties and serve their residents. Law may either grant some benefits of take them away based on individual's activities and if these activities are performed in different Member State may not matter. People are either unaware that they should report something to a Member State, or they refuse to report that knowingly. Thus, matching people’s records bilaterally seems to include promise to mitigate several risks for states. The risk of incorrect matching and the risk of not finding a match when there really is one – both may have significant negative consequences due to the scale of the process.
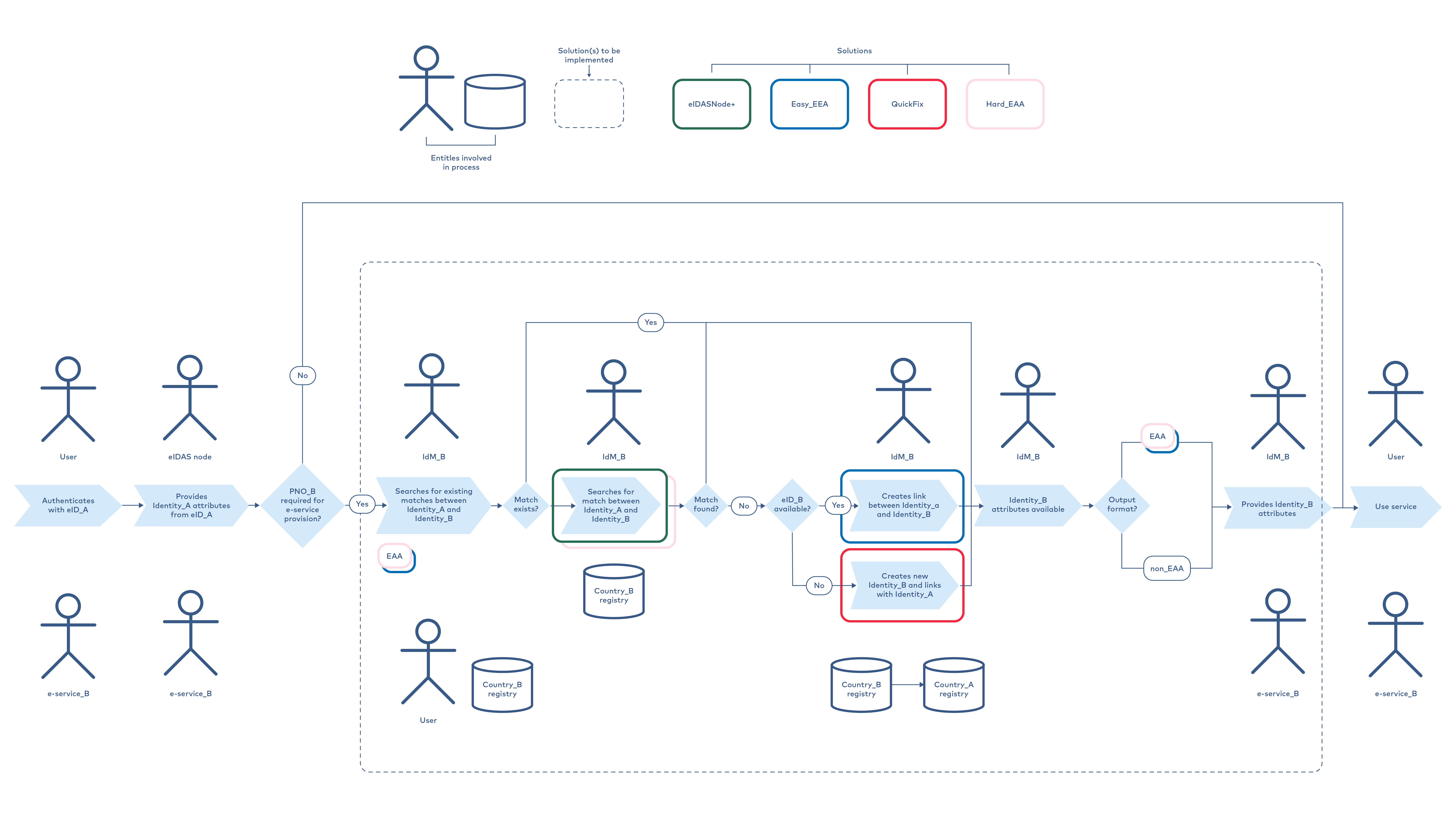
The 10 possible solutions to address these three scenarios are as follows.
Exresidence
Every country issue through digital process local eID mean (e.g., to EUDIW - EU Digital Identity Wallet, or a separate token) to cross-border users trying to access that country's e-services. This way a person gets eID mean that local e-service can operate with, and user will be enabled to enjoy e-services in other country and access his/her personal records. With this solution identity matching process for potential later cross-border identity or record matching remains unsolved, as no identity matching is performed.
+ | User can swiftly access cross-border e-services. |
- | Most countries must develop digital issuance process for their eID mean(s), which requires also principal legal changes. |
- | The problem of identity matching is not solved but pushed one step further. |
QuickFix
Convert personal identification number's physical issuance process into digital remote video identity verification process and integrate this process into current business flow of e-services’ usage. Proposed digital identity creation (personal identification number issuance) is based on combination of eID authentication and capture of biometric identifier (facial image). Processing facial images depends on country’s practices. The process ends with establishing connection between two countries’ personal identification numbers in local population registry.
+ | Users can access cross-border e-service through purely digitally provided workflow. |
+ | Remote video identity solutions can be designed to meet every country’s requirement. |
+ | Physical process can be replaced by a digital one – potential efficiency. |
- | Countries must develop new digital business processes and create respective legal framework influencing existing principles. |
- | Technologically more complex process, which requires involvement of knowledge from additional fields of expertise. |
Hard_EAA
Country of an e-service provider concludes identity matching using eID mean from other country and data from local population registry. Output of identity matching process is delivered in format of electronic attestation of attributes (EAA), which includes link between personal identification numbers of two countries and other necessary PII. EAA is delivered to e-service that is being accessed by user. In addition, EAA is delivered to the user, so a person can use it as identity matching evidence during future interactions with e-services.
+ | Users can access cross-border e-service through purely digitally provided workflow. |
+ | Minor or no changes to user experience, as process is based on regular usage of eID mean. |
- | Countries must establish a framework for legal recognition of EAAs, their technical format, exchange/storage mechanisms and validation principles. |
Easy_EAA
Service, which allows "pairing" of eID means of two countries. Country of an e-service provider concludes identity matching using eID means at person’s hand. Identity matching service establishes a link between two identities based on attributes received from eID means of both countries. Ground for match bases on uninterrupted process performed by authoritative party during which authentication with both eID means is performed, thus identities of two countries can be linked.
Output of identity matching process is delivered in format of electronic attestation of attributes (EAA), which includes link between personal identification numbers of two countries and other necessary PII. EAA is delivered to e-service that is being accessed by user. In addition, EAA is delivered to the user, so a person can use it as identity matching evidence during future interactions with e-services.
+ | Users can access cross-border e-service through purely digitally provided workflow. |
+ | Minor or no changes to user experience, as process is based on regular usage of eID means. |
- | Not every user has eID meanings from two countries at hand. |
- | Countries must establish a framework for legal recognition of EAAs, their technical format, exchange/storage mechanisms and validation principles. |
eIDAS_0
User is granted access to cross-border e-services based on eID mean of his/her country of residence. Identity matching is performed relying on attributes received from eID mean and PII coming from population registry of cross-border e-service location. Result of identity matching will have use for the countries general identity management purposes and is made available to e-services, whereas e-services operate in their internal processes based on personal identification number delivered by eID mean of other country. E-services must be able to operate with a foreign personal identification number.
+ | No changes to user experience, as the process is based on regular usage of eID mean. |
- | Significant impact (impossible to deploy) on business logic of e-services. |
eIDASNode+
Every foreign identity will be assigned a local personal identification number. After authentication with eID mean through eIDAS node e-services approach local identity matching service for retrieval of local personal identification number of user. E-services are required to implement in their user authentication flow an intermediate step for API request towards identity matching service for retrieval of local personal identification number. Identity matching service either finds a match form (population) registry or creates new local identity. Output of identity matching process includes link between personal identification numbers of two countries and other necessary PII.
+ | Minor or no changes to user experience, as process is based on regular usage flow of eID means. |
+ | E-services can operate based on local personal identification number. |
E-services can operate based on local personal identification number.Defense
Biometric identity verification (1:1) is added to the eID authentication process to perform identity matching process. A person’s facial image is captured during authentication step by identity matching service using remote video identity verification technology. Biometric verification is performed based on user facial images captured from video session and facial image retrieved from biometric database of e-service’s country of location.
+ | Usage of additional strong attributes, that provides required level of assurance for identity management that might not be achievable with eID mean’s attributes only. |
- | Not all countries store biometric data of residents. |
- | Technologically more complex process, which requires involvement of knowledge from additional fields of expertise. |
- | Usage of biometric identifiers for identity verification in context of cross-border e-service usage can be legally challenging. |
Hinting
Identity matching is performed based on minimum mandatory data set provided by eIDAS node and using country specifically available additional attributes (in addition to 4 mandatory attributes) from eID means. Input for identity matching process is collected during eID authentication and matching system attempts to execute the process based on limited attributes and PII available in local population registry.
+ | No changes to user experience, as the process is based on regular usage of eID mean. |
- | Limited number of attributes available, which probably require usage of supplementary procedures for establishing identity match. |
- | Usage of e-service might fall into physical process. |
- | Current modus operandi, which does not work in practice. |
Bonding
Process involving interaction of backend systems of two countries, where biometric verification (1:1) or identification (1:n) is part of identity matching process. Proceedings between two countries are executed based on triggers, which are not related to direct activities of user during consuming of e-service (e.g., migration events, activities in non-residential country, etc.) whereas person him/herself is not involved in the matching process. Country in necessity for identity matching initiates procedure, where PII and facial images are retrieved from databases of both countries. Following steps on top of PII data matching include facial image verification/identification either by country in necessity or by both countries.
+ | Usage of additional strong attributes, that provides required level of assurance for identity management that might not be achievable with PII only. |
- | Not all countries store biometric data. |
- | Technologically more complex process, which requires involvement of knowledge from additional fields of expertise. |
- | Usage of facial image for biometric verification/identification in context of cross-border e-service usage can be legally challenging. |
Binding
Process involving data exchange between population registries of two countries, which is followed by identity matching process. Proceeding is initiated by backends systems following defined triggers (e.g. migration events, activities in non-residential country, etc.) whereas person him/herself is not involved in the matching process. Country in necessity for identity matching initiates process for exchange of person’s PII between two countries and executes identity matching.
+ | Solution operates based on common PII used for identity management. |
- | Reliability of matching outcome might be questionable, as partial matches are expected to have significant proportion due to person him/herself not being involved in proceedings. |
- | “Partial matches” require manual processing. |
Evaluation of 10 preliminary solutions was conducted by combining 2 methods. First the 10 possible solutions were introduced at a seminar, where the participants were asked to evaluate the suitability of each solution by rating them on a scale from 1 to 5. Before casting the votes, participants and solutions’ presenters discussed each solution and questions from audience were answered or remarks taken. The results of voting are depicted on Figure 13, where average score and distribution of provided points are depicted for each solution. Score of voting is summarized in Table 17, showing the ranking of solutions.
Secondly, conductors of analysis evaluated the strengths and weaknesses of all 10 solutions. Based on identified substantial weaknesses (above marked bold) and low efficiencies 6 solutions were discarded from further analysis. It must be noted that the 4 most preferred solutions voted by participants of Tallinn workshop and selected through analysis did match 100%.
In Ch. 3.2 the four most potential solutions will be described in more detail.

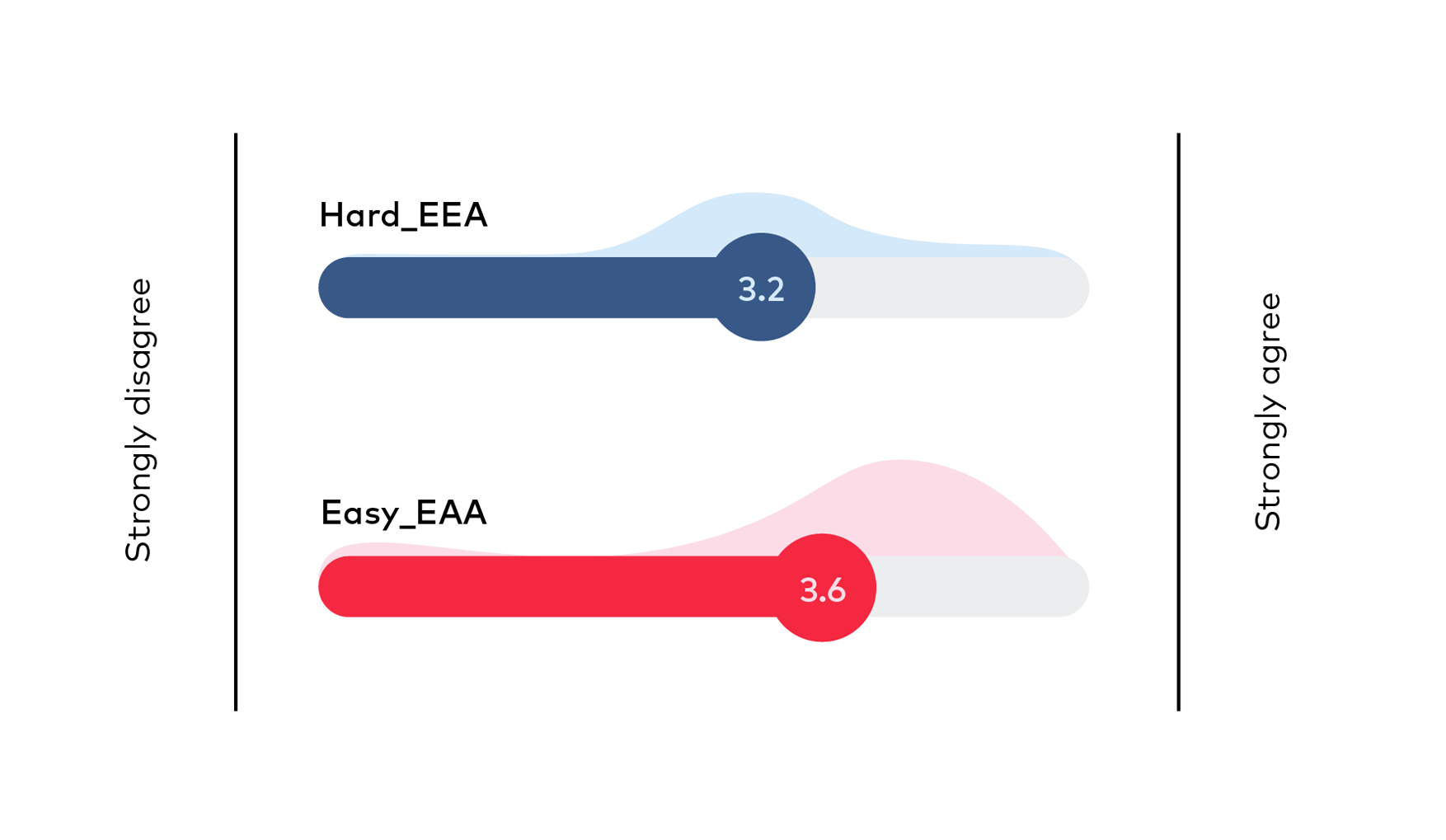
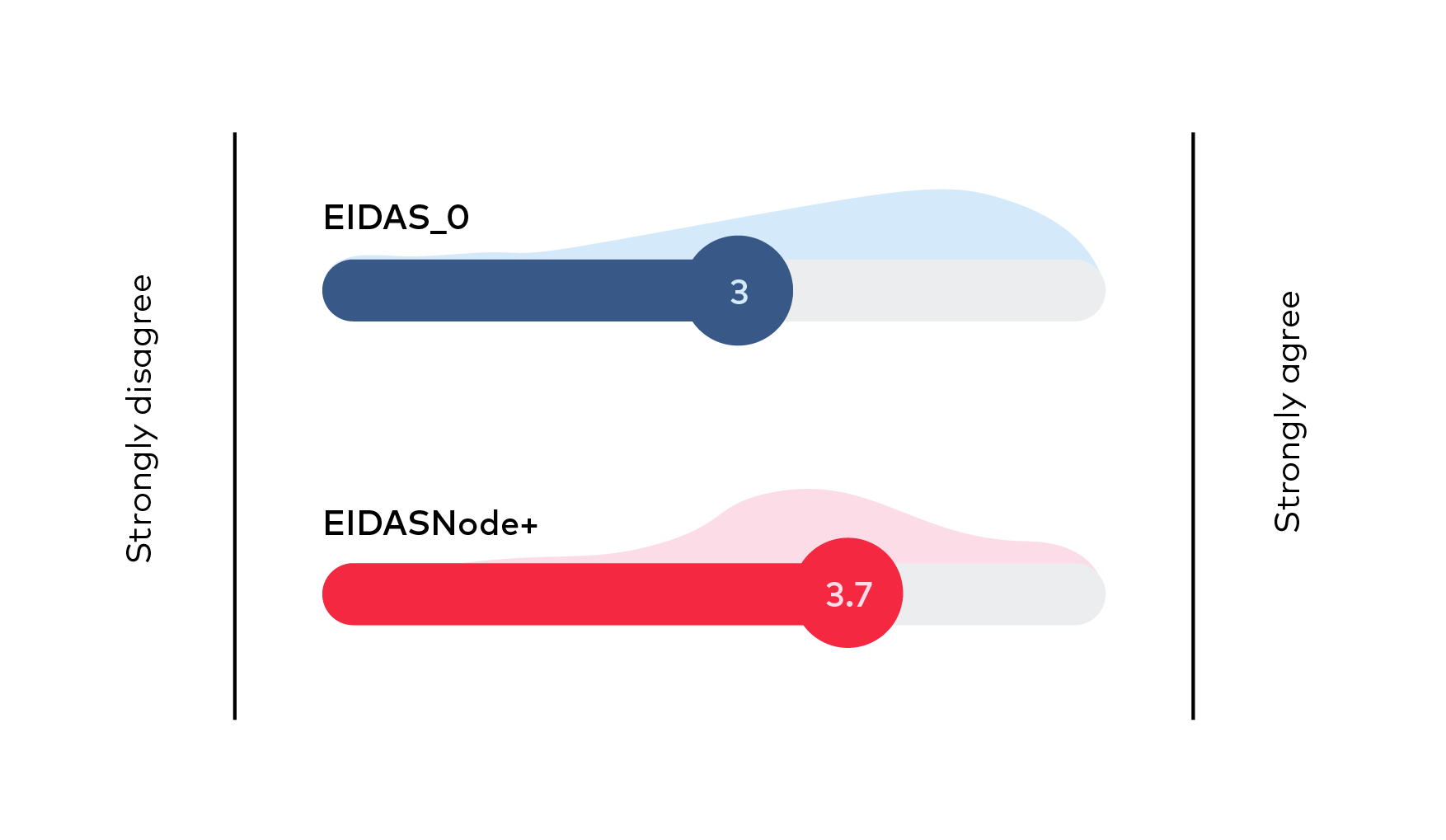
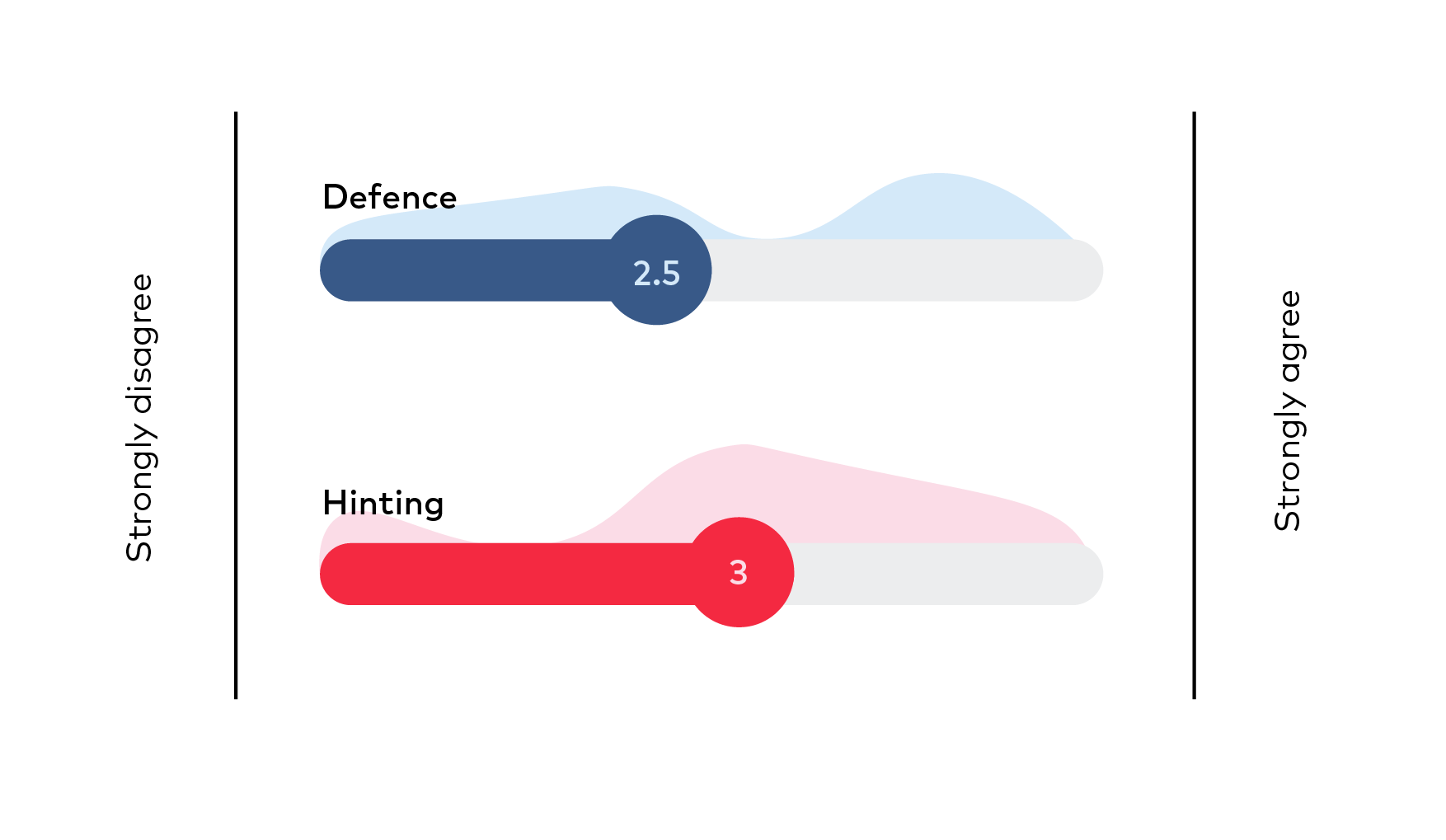
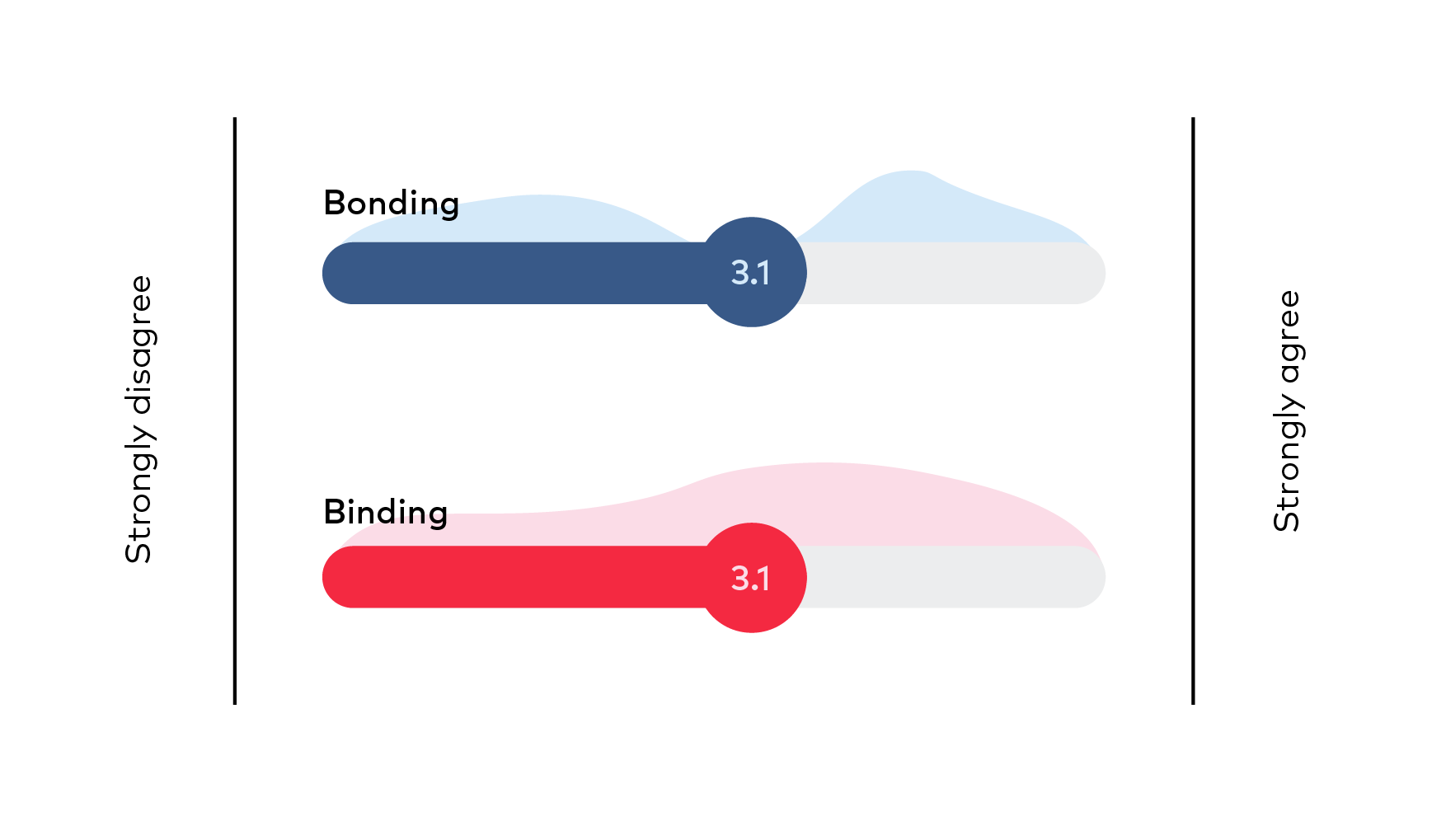
Figure 13 Preferences of solutions from Tallinn workshop participants (average score and distribution of points)
Solution | Score |
eIDASNode+ | 3,7 |
Easy_EAA | 3,6 |
QuickFix | 3,5 |
Hard_EAA | 3,2 |
Bonding | 3,1 |
Binding | 3,1 |
exResidence | 3,0 |
eIDAS_0 | 3,0 |
Hinting | 3,0 |
Defence | 2,5 |
Table 17 Ranking of solutions based on poll with Tallinn workshop participants
3.2 Description of highest potential solutions
The four highest potential solutions are the following:
- eIDASNode+
- Easy_EAA
- QuickFix
- Hard_EAA
We will elaborate on these solutions in more detailed trough personas, epic, user stories and use cases.
3.2.1 eIDASNode+
For every foreign identity a local personal identification number will be assigned. After authentication with eID mean through eIDAS node, e-services approach local identity matching service for retrieval of local personal identification number of user. E-services are required to implement in their user authentication flow an intermediate step for API request towards identity matching service for retrieval of local personal identification number. Identity matching service either finds a match form (population) registry or creates new local identity. Identity matches can be already established during some administrative procedures undergone earlier (e.g. registering residence).
Output of identity matching process delivered to e-service includes link between personal identification numbers of two countries and other necessary PII. Exchange of data about matched identities between two involved countries is essential for successful deployment of once only principle and trustworthy identity management in Nordic-Baltic region.
Data exchange between countries can be performed based on to be established framework defining principles for identity matching process and acceptance of matched identities between countries in Nordic-Baltic region.
E-services in receiving country continue operating with local personal identification number.
Personas
John
- is a resident of country_A,
- has eID_A mean from country_A,
- has been awarded bachelor’s degree (diploma) at university_B located in country_B,
- wants to apply for master’s degree at university_A in country_A,
- is eager to improve his educational qualification and is thereof very co-operative (has no problem with submitting PII beyond eID scheme content).
University_A
- has e-service for submitting applications for admission to university,
- e-service users can authenticate with eID means supported by eIDAS node,
- must verify holding of bachelor’s degree,
- must match the identity of diploma holder with the identity of authenticated user.
University_B
- has e-service, which provides access to diploma records,
- e-service users can authenticate with eID means supported by eIDAS node,
- must match the identity of diploma holder with the identity of authenticated user.
Country_A IdM service provider (IdM_A)
- has access to PII data of country_A residents,
- has processes and logic in place for IdM,
- has access to data of matched identities, authority to create matches between identities and create new identity in country_A,
- has data exchange with IdM_B for sharing matching results involving identities of country_A and country_B,
- accepts and trusts matching results delivered by IdM_B, which involve identities of country_A and country_B.
Country_B IdM service provider (IdM_B)
- has access to PII data of country_B residents,
- has processes and logic in place for IdM,
- has access to data of matched identities, authority to create matches between identities and create new identity in country_B,
- has data exchange with IdM_A for sharing matching results involving identities of country_A and country_B,
- accepts and trusts matching results delivered by IdM_A, which involve identities of country_A and country_B.
Figure 14 Use case on EIDASNODE+
Epic
As John, I want to prove the obtaining of bachelor’s degree in university_B to apply for master’s degree in university_A.
User stories
As John, I want to retrieve and present my diploma through e-services of universities to facilitate the process.
As John, I want to identify myself with my eID_A to provide assurance of my identity.
As John, I want diploma to be matched with my identity_A to prove obtaining of bachelor’s degree.
As university_A/B, I want to provide e-services for document/process management for optimizing workload.
As university_A/B, I want to enable access to e-services with eID means supported by eIDAS node for reliable authentication of users.
As university_A/B, I want to rest assured that identities of diploma holder and authenticated user are matching for avoidance of misusage/fraud.
Use cases
UC#1 User authenticates with eID_A to university_B e-service.
- University_B e-service authenticates user through eIDAS node and eID_A provider and receives identity attributes for eID_A.
UC#2 User submits request for collecting the bachelor’s degree diploma.
UC#3 University_B e-service interacts with IdM_B for establishing the alumni identity.
- University_B e-service delivers eID_A attributes to IdM_B.
- IdM_B searches for existing matches between Id_A and Id_B.
- If not found, then IdM_B searches from Country_B registry match for Id_A. Match between Id_A and Id_B is created in Country_B registry and stored with Id_A attributes. IdM_A is notified about created match of identities and data is stored in Country_A registry.
- If no match is found, then IdM_B creates new Id_B in Country_B registry. Match between Id_A and Id_B is created in Country_B registry and stored with Id_A attributes. IdM_A is notified about created match of identities and data is stored in Country_A registry.
- IdM_B provides Id_B attributes to University_B e-service.
UC#4 University_B e-service displays to user diploma evidence.
UC#5 User downloads the diploma evidence.
UC#6 User authenticates with eID_A to university_A e-service.
UC#7 User submits application for admission to master’s programme.
- User uploads the diploma as attachments to application.
UC#8 University_A e-service interacts with IdM_A for verifying match between Id_A and Id_B.
- University_A e-service delivers eID_A attributes to IdM_A.
- IdM_A searches for existing matches between Id_A and Id_B.
- Existing match is found due to IdM_B having shared result of earlier matching process conducted with User’s identities.
- IdM_A confirms match of two identities and provides Id_B attributes to University_A e-service.
UC#9 University_A e-service validates IdM_A response and diploma records.
- Upon successful validation of IdM_A response and diploma records, User’s application is accepted.
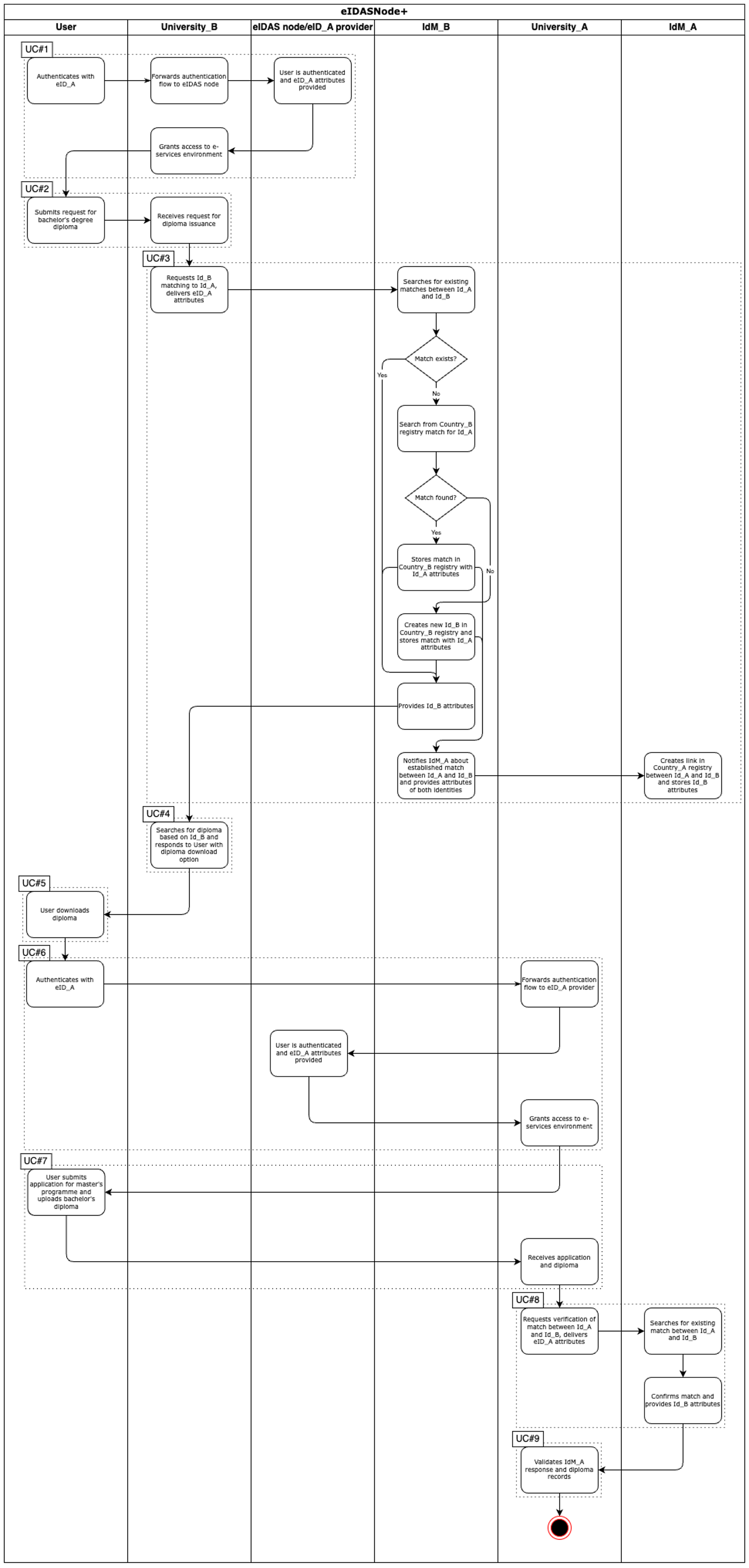
Figure 15 EIDASNode+ detailed WORKFLOW
3.2.2 Easy_EAA
Service, which allows "pairing" of eID means of two countries. Country of e-service provider concludes identity matching using eID means at person’s hand. Identity matching service establishes a link between two identities based on attributes received from eID means of both countries. Ground for match bases on uninterrupted process performed by authoritative party during which authentication with both eID means is performed, thus identities of two countries can be linked.
Output of identity matching process is delivered in format of electronic attestation of attributes (EAA), which includes link between personal identification numbers of two countries and other necessary PII. EAA is delivered to e-service that is being accessed by user. In addition, EAA is delivered to the user, so a person can use it as identity matching evidence during future interactions with e-services.
Personas
John
- is resident of country_A,
- has eID_A mean from country_A,
- has eID_B mean from country_B,
- has been awarded bachelor’s degree (diploma) at university_B located in country_B,
- wants to apply for master’s degree at university_A in country_A,
- is eager to improve his educational qualification and is thereof very co-operative (has no problem with submitting PII beyond eID scheme content).
University_A
- has e-service for submitting applications for admission to university,
- e-service users can authenticate with eID means issued in country_A,
- must verify holding of bachelor’s degree,
- must match identity of diploma holder with the identity of authenticated user,
- has capability to process EAAs.
University_B
- has e-service, which provides access to diploma records,
- e-service users can authenticate with eID means issued in country_B,
- must match identity of diploma holder with the identity of authenticated user,
- has capability to process EAAs.
Country_A IdM service provider (IdM_A)
- has access to PII data of country_A residents,
- has processes and logic in place for IdM,
- has process for reliably pairing of eID means of two countries,
- has access to data of matched identities, authority to create matches between identities and create new identity in country_A,
- has data exchange with IdM_B for sharing matching results involving identities of country_A and country_B,
- accepts and trusts matching results delivered by IdM_B, which involve identities of country_A and country_B,
- issues matching results in format of EAAs.
Country_B IdM service provider (IdM_B)
- has access to PII data of country_B residents,
- has processes and logic in place for IdM,
- has process for reliably pairing of eID means of two countries,
- has access to data of matched identities, authority to create matches between identities and create new identity in country_B,
- has data exchange with IdM_A for sharing matching results involving identities of country_A and country_B,
- accepts and trusts matching results delivered by IdM_A, which involve identities of country_A and country_B,
- issues matching results in format of EAAs.
Figure 16 Use case for EASY_EAA
Epic
As John, I want to prove the obtaining of bachelor’s degree in university_B to apply for master’s degree in university_A.
User stories
As John, I want to retrieve and present my diploma through e-services of universities to facilitate the process.
As John, I can identify myself with my eID_A and eID_B to provide assurance of my identity in both countries.
As John, I want diploma to be matched with my identity_A to prove obtaining of bachelor’s degree.
As university_A/B, I want to provide e-services for document/process management for optimizing workload.
As university_A/B, I want to enable access to e-services with eID means supported by eIDAS node for reliable authentication of users.
As university_A/B, I want to rest assured that identities of diploma holder and authenticated user are matching for avoidance of misuse/fraud.
Use cases
UC#1 User authenticates with eID_B to university_B e-service.
- University_B e-service authenticates user through eID_B provider and receives identity attributes for eID_B.
UC#2 User submits request for collecting the bachelor’s degree diploma.
UC#3 University_B validates eID_B attributes against diploma records and displays to user diploma evidence.
UC#4 User downloads the diploma evidence.
UC#5 User authenticates with eID_A to university_A e-service.
- University_A e-service authenticates user through eID_A provider and receives identity attributes for eID_A.
UC#6 User submits application for admission to master’s programme.
- User uploads diploma as attachments to application.
UC#7 University_A e-service interacts with IdM_A for verifying match between Id_A and Id_B.
- IdM_A searches for existing matches between Id_A and Id_B.
- If not found, then IdM_A searches from Country_A registry match for Id_B. Match between Id_A and Id_B is created in Country_A registry and stored with Id_B attributes. IdM_B is notified about created match of identities in format of EAA and data is stored in Country_B registry.
- If no match found, then IdM_A requests User through open session with University_A to authenticate with eID_B and eID_A in sessions under control of IdM_A. Once User has authenticated with both eID_B and eID_A in the session created by IdM_A the match between both identities is created. IdM_B is notified about created match of identities in format of EAA and data is stored in Country_B registry.
- IdM_A confirms match of identities and provides Id_B attributes to University_A e-service in format of EAA.
UC#8 University_A e-service validates IdM_A matching result EAA against diploma attributes.
- Upon successful validation of IdM_A response and diploma records, User’s application is accepted.
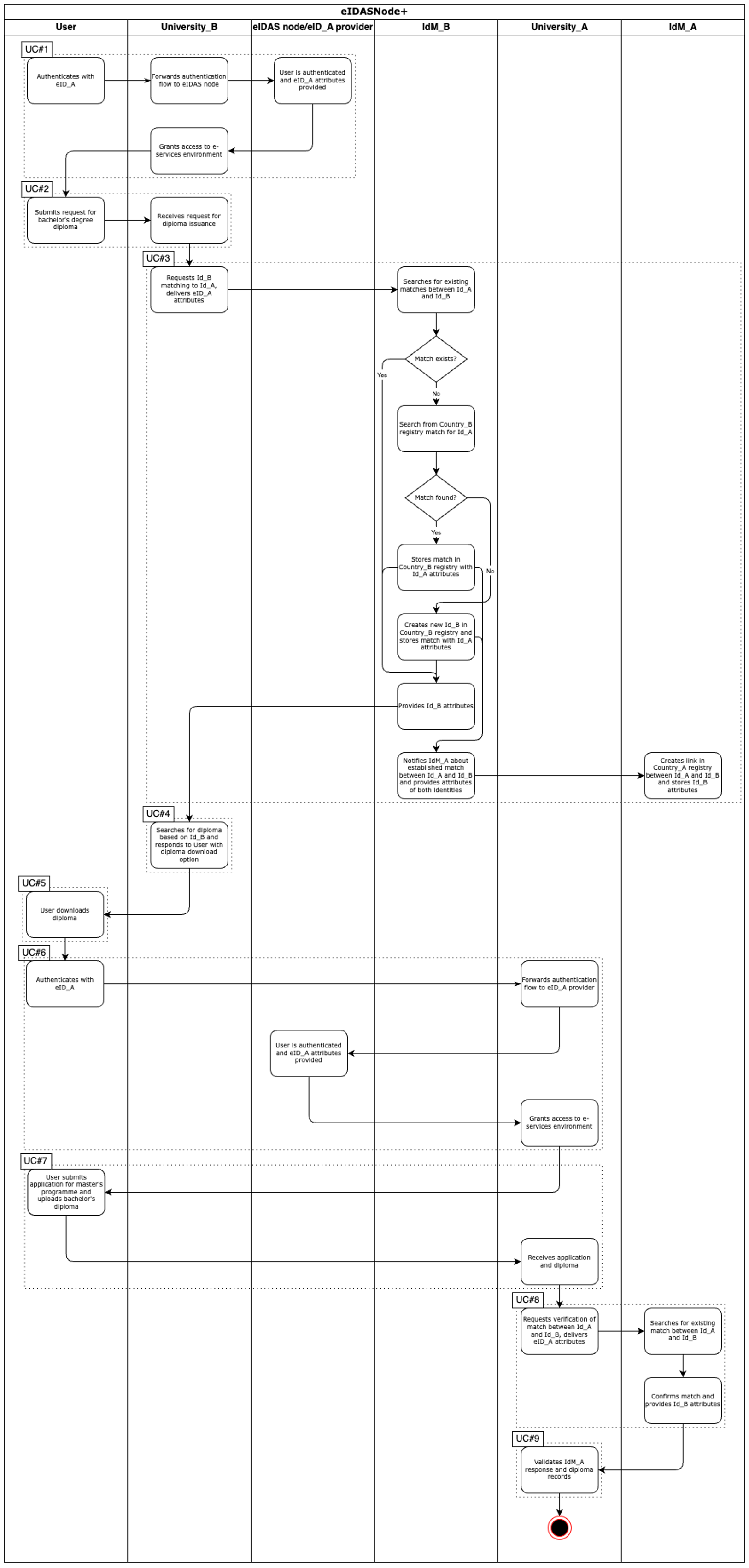
Figure 17 Easy_EAA detailed WORKFLOW
3.2.3 QuickFix
Convert personal identification number's physical issuance process into digital remote video identity verification process and integrate this process into current business flow of e-services’ usage. Proposed digital identity creation (personal identification number issuance) is based on combination of eID authentication and capture of biometric identifier (facial image). Processing facial images depends on country’s practices. The process ends with establishing connection between two countries’ personal identification numbers in local population registry.
Personas
John
- is resident of country_A,
- has eID_A mean from country_A,
- has been awarded bachelor’s degree (diploma) at university_B located in country_B,
- wants to apply for master’s degree at university_A in country_A,
- is eager to improve his educational qualification and is thereof very co-operative (has no problem with submitting PII beyond eID scheme content).
University_A
- has e-service for submitting applications for admission to university,
- e-service users can authenticate with eID means supported by eIDAS node,
- must verify holding of bachelor’s degree,
- must match the identity of diploma holder with the identity of authenticated user.
University_B
- has e-service, which provides access to diploma records,
- e-service users can authenticate with eID means supported by eIDAS node,
- must match the identity of diploma holder with the identity of authenticated user.
Country_A IdM service provider (IdM_A)
- has access to PII data of country_A residents,
- has processes and logic in place for IdM,
- has access to data of matched identities, authority to create matches between identities and create new identity in country_A registry,
- has data exchange with IdM_B for sharing matching results involving identities of country_A and country_B,
- accepts and trusts matching results delivered by IdM_B, which involve identities of country_A and country_B.
Country_B IdM service provider (IdM_B)
- has access to PII data of country_B residents,
- has processes and logic in place for IdM,
- has access to data of matched identities, authority to create matches between identities and create new identity in country_B registry,
- has data exchange with IdM_A for sharing matching results involving identities of country_A and country_B,
- accepts and trusts matching results delivered by IdM_A, which involve identities of country_A and country_B.
Figure 18 Use case for QUICKFIX
Epic
As John, I want to prove the obtaining of bachelor’s degree in university_B to apply for master’s degree in university_A.
User stories
As John, I want to retrieve and present my diploma through e-services of universities to facilitate the process.
As John, I want to identify myself with my eID_A to provide assurance of my identity.
As John, I want diploma to be matched with my identity_A to prove obtaining of bachelor’s degree.
As university_A/B, I want to provide e-services for document/process management for optimizing workload.
As university_A/B, I want to enable access to e-services with eID means supported by eIDAS node for reliable authentication of users.
As university_A/B, I want to rest assured that identities of diploma holder and authenticated user are matching for avoidance of misuse/fraud.
Use cases
UC#1 User authenticates with eID_A to university_B e-service.
- University_B e-service authenticates user through eIDAS node and eID_A provider and receives identity attributes for eID_A.
UC#2 User submits request for collecting the bachelor’s degree diploma.
UC#3 University_B e-service interacts with IdM_B for establishing the alumni identity.
- University_B e-service delivers eID_A attributes to IdM_B.
- IdM_B searches for existing matches between Id_A and Id_B.
- If not found, then IdM_B searches from Country_B registry match for Id_A. Match between Id_A and Id_B is created in Country_B registry and stored with Id_A attributes. IdM_A is notified about created match of identities and data is stored in Country_A registry.
- If no match is found, then IdM_B initiates remote video identification session and directs User to facial image capturing procedure.
- User presents facial image.
- IdM_B system performs verification of captured facial image.
- IdM_B engages human operator in necessity for clarification of additional information.
- IdM_B creates new Id_B in Country_B registry. Match between Id_A and Id_B is created in Country_B registry and stored with Id_A attributes. IdM_A is notified about created match of identities and data is stored in Country_A registry.
- IdM_B provides Id_B attributes to University_B e-service.
UC#4 University_B e-service displays to user diploma evidence.
UC#5 User downloads the diploma evidence.
UC#6 User authenticates with eID_A to university_A e-service.
UC#7 User submits application for admission to master’s programme.
- User uploads the diploma as attachments to application.
UC#8 University_A e-service interacts with IdM_A for verifying match between Id_A and Id_B.
- University_A e-service delivers eID_A attributes to IdM_A.
- IdM_A searches for existing matches between Id_A and Id_B.
- Existing match is found due to IdM_B having shared result of earlier matching process conducted with User’s identities.
- IdM_A confirms match of two identities and provides Id_B attributes to University_A e-service.
UC#9 University_A e-service validates IdM_A response and diploma records.
- Upon successful validation of IdM_A response and diploma records, User’s application is accepted.
Figure 19 Quickfix detailed WORKFLOW
3.2.4 Hard_EAA
Country of e-service provider concludes identity matching using eID mean from other country and data from local population registry. Output of identity matching process is delivered in format of electronic attestation of attributes (EAA), which includes link between personal identification numbers of two countries and other necessary PII. EAA is delivered to e-service that is being accessed by user. In addition, EAA is delivered to the user, so a person can use it as identity matching evidence during future interactions with e-services.
Personas
John
- is resident of country_A,
- has eID_A mean from country_A,
- has been awarded bachelor’s degree (diploma) at university_B located in country_B,
- wants to apply for master’s degree at university_A in country_A,
- is eager to improve his educational qualification and is thereof very co-operative (has no problem with submitting PII beyond eID scheme content).
University_A
- has e-service for submitting applications for admission to university,
- e-service users can authenticate with eID means supported by eIDAS node,
- must verify holding of bachelor’s degree,
- must match identity of diploma holder with the identity of authenticated user,
- has capability to process EAAs.
University_B
- has e-service, which provides access to diploma records,
- e-service users can authenticate with eID means supported by eIDAS node,
- must match identity of diploma holder with the identity of authenticated user,
- has capability to process EAAs.
Country_B IdM service provider (IdM_B)
- has access to PII data of country_B residents,
- has processes and logic in place for IdM,
- has access to data of matched identities, authority to create matches between identities and create new identity in country_A,
- has data exchange with IdM_B for sharing matching results involving identities of country_A and country_B,
- accepts and trusts matching results delivered by IdM_B, which involve identities of country_A and country_B,
- issues matching results in format of EAAs.
Figure 20 Use case for Hard_EEA
Epic
As John, I want to prove the obtaining of bachelor’s degree in university_B to apply for master’s degree in university_A.
User stories
As John, I want to retrieve and present my diploma through e-services of universities to facilitate the process.
As John, I want to identify myself with my eID_A to provide assurance of my identity.
As John, I want diploma to be matched with my identity_A to prove obtaining of bachelor’s degree.
As university_A/B, I want to provide e-services for document/process management for optimizing workload.
As university_A/B, I want to enable access to e-services with eID means supported by eIDAS node for reliable authentication of users.
As university_A/B, I want to rest assured that identities of diploma holder and authenticated user are matching for avoidance of misuse/fraud.
Use cases
UC#1 User authenticates with eID_A to university_B e-service.
- University_B e-service authenticates user through eIDAS node and eID_A provider and receives identity attributes for eID_A.
UC#2 User submits request for collecting the bachelor’s degree diploma.
UC#3 University_B e-service interacts with IdM_B for establishing the alumni identity.
- University_B e-service delivers eID_A attributes to IdM_B.
- IdM_B searches for existing matches between Id_A and Id_B.
- If not found, then IdM_B searches from Country_B registry match for Id_A. Match between Id_A and Id_B is created in Country_B registry and stored with Id_A attributes. IdM_A is notified about created match of identities in format of EAA and data is stored in Country_A registry.
- If no match is found, then IdM_B creates new Id_B in Country_B registry. Match between Id_A and Id_B is created in Country_B registry and stored with Id_A attributes. IdM_A is notified about created match of identities in format of EAA and data is stored in Country_A registry,
- IdM_B confirms match of identities and provides Id_B attributes to University_A e-service in format of EAA.
UC#4 University_B e-service displays to user identity matching EAA and diploma evidence.
UC#5 User downloads the identity matching EAA and diploma evidence.
UC#6 User authenticates with eID_A to university_A e-service.
UC#7 User submits application for admission to master’s programme.
- User uploads the identity matching EAA and diploma as attachments to application.
UC#8 University_A e-service validates provided identity matching to EAA and diploma.
- Upon successful validation of EAA and diploma records, User’s application is accepted.
Figure 21 Hard_EEA detailed WORKFLOW
3.3 Suggestions for Nordic-Baltic region
In general, our proposed solution consists of answers to two crucial questions:
- How actually member state e-services would be able to smoothly start serving non-residents of a given member state regardless of the user being a returning user with changed residency or a new user?
- How potential match between identities from different member states be made with the least amount of effort on the level of required assurance and following once only principle?
As we considered that member state services architecture will remain dependent on the local identity data structure for a while, then we deemed priority to implement “change on border” type of solution. This means everyone who enters e-service in a member state will be granted the ability to explain their identity in a format that is known in local ecosystems.
For that to happen our suggestion is to change it through proxy like eIDAS Node that is described in detail in “eIDASNode+” scenario, where we extend the existing framework to accommodate the multitude of identities. The implementation of identity matching solution must respect the fact that not all e-services require local identity. Named e-services should not be impacted by the change and must be able to operate with setup that corresponds to current eIDAS node and business logic.
We still considered that direct connection to e-services should be regarded as well, and this can be done through EAA (which is created through completing of “Hard_EAA” or “Easy_EAA” scenario) as part of authentication and authorization process.
Further, if a person has an EAA that connects different identities and that individual needs to prove some rights (eligibility) or needs to create connections to any dataset, then person will be enabled to present and prove that claim, even if through a manual process. With working eID and EAA all the evidence needed is immediately at persons disposal and ready to be presented for a decision.
Dependent of the agreed objectives, identity matching solution can be built up this way that “eIDASNode+” can be used as core solution or foundation for provisioning the service. There are several countries in Nordic-Baltic region, who either have deployed solution common to “eIDASNode+” or have made plans following mindset of “eIDASNode+”. Other solutions can be incorporated into logic of “eIDASNode+” following the added value that they provide either by facilitating matching process (e.g., “Easy_EAA” pairing of eID means, “QuickFix” digitizes process of new identity creation) or providing interoperable scheme in format of EAA (“Easy_EAA”, “Hard_EAA”) for distribution and further utilization of identity matching results. Nevertheless, all 4 solutions do have properties that allow their deployment as standalone solutions.
To answer the second question, identity matching service availability together with ability to find existing and assign new member state specific identifiers is the cornerstone of the proposal. It must be noted, to fulfil targets of SDGR ability to assign new member state identifiers through digital process is of same importance as having capability to match identities of different members states.
In most countries such a service exists but is often not available remotely. Our QuickFix scenario improves the availability of receiving member state specific identity attributes and produces. Also, the Easy_EAA is easy to implement alongside any existing identity matching allowing most of the work to happen as self-service. The Hard_EAA model builds on the fact that e-Service user is known to have a high level of assurance for one member state and the next member state can rely on the first, therefore. That again improves the availability of identity matching services.
There is substantial potential for efficiency in sharing the matching service results to the member state from where the matched identity is from. Matching made in one country should not be contested by another country and both countries could use the match for translating identity in their member state services. EAA format allows data to be shared and checked for validity in quite a general sense whereby the integrity and authenticity of data is well protected. Solution for exchange and recognition of EAAs between registries of member states is subject for further design and agreement.
Common rules of making the match could also mean that matching will have its own “level of assurance” to indicate what process and data was used to match the identities. The highest level of assurance should mean that the matching could be trusted to hold true in any transaction regardless of the context. Lower levels could be appointed if the assurance holds true only in clearly one sector specific context (healthcare, construction, taxation, etc.) or where there was a need to make the match with clear lack of data and associated risks allowed still to pursue.
While dealing with data exchange between member states and ensuring the trustworthy results of matching process, the necessity for data sharing between member states’ registries during identity matching process must be noted. During interviews with Nordic and Baltic countries the need to extend scope of attributes available for identity matching process was expressed multiple times. Not limiting to but attributes like ‘nationality’ and ‘place of birth’ have been regarded as records what would facilitate matching process and provide required trustworthiness. Although eIDAS node has several attributes (incl. ‘place of birth’) that may be distributed, then due to their optional nature these attributes are mostly not available to relying parties. Accordingly, such additional attributes could be shared through data exchange of registries in countries whose identities are involved in a particular matching process.
Actionplan to implement suggestions
The following must be done, to implement proposed solutions:
- Define EAA standard to use and specify content (e.g. OpenID Connect for Verifiable Credentials (OIDC-VC) for electronic usage, but we do recommend PDF to support F2F interactions as well). Although the content of the attestation is not too complex, issues like data minimization and privacy preservation may lead to some difficulties. Standards that exist allow interpretations that do not guarantee interoperability on attribute level, so specific implementation must be agreed. Also, we note that the agreement must be ready to be changed as the maturity of eIDAS defined attribute attestation service evolves in coming years.
- Create common extension or use existing one to allow eIDAS Node to replace incoming identity with local one before reaching e-Service provider. Organizationally the identity matching data and the service that translates the foreign eID’s into locally acceptable ones, does not need to be bundled with eIDAS Node hosting, but that might ease the implementation. It is important that the service is usable by eIDAS Node and that is supported in the product lifecycle as an extension. This may need cooperation agreement with European Commission that is responsible for the building blocks development.
- Review national legislations for processing of personal data in terms, that would support deployment of once only principle and in justified use cases facilitate identity management processes in a user controlled manner. Initiate legal changes necessary for introduction of proposed procedural and technical activities.
- Agree on NBCM level that electronic identification of one’s resident on “high” level of assurance must be accepted as proof of identity on the same level as using physical identity documents from that country and to identify physical person, countries grant to each other similar rights and obligations what are contextually needed.
- Formalize sharing of the matched identity data between countries. Establish framework defining principles for identity matching process and acceptance of matched identities in Nordic-Baltic region. It should give requirements for:
- Accepted sources for identity attributes (e.g., eID means, identity documents, cross-border data exchanges between registries),
- Handling identity attributes (e.g., minimum data set, encoding of characters),
- Defining the level of assurance for results of identity matching process dependent of identity attributes’ sources and procedures in involved case,
- Data governance rules, protection, and mechanisms for supervision for data handling (e.g., notification to matched identity about established cross-border connection with other identity, enable users to view events accessing their data).
Harmonized and enforced requirements allow participants of framework to trust each other’s matching results and enhance identity management in region through cost-effective approach.
- Enable data exchange of attributes between countries, deemed necessary for identity matching process.
- Address the issue of derived personal identification number usage as value for person’s unique identifier delivered by eID schema in a cross-border context. Following EC published information there are several countries in Nordic-Baltic region, who implement such practice. Handling of derived personal identification numbers adds remarkable complexity layer to identity matching process and to usage of matching results, if created evidence does not contain personal identification number values that are operated domestically or communicated to other countries (i.e., receiving country specific derivation).
- Amend domestic legislation and processes so that creation of identities through digital process would be allowed. Currently persons accessing cross-border e-services without having an e-service provider’s domestic country’s personal identification number are queued in virtual “waiting rooms”. Passage through a virtual waiting room is granted only after completion of specific physical activities in receiving country. Digital transformation of physical procedures meets the aim of SDG regulation. Dependent of country specifics, the identities created through digital processes could have dedicated level of assurance or status in country’s identity management system.
What will the future safety concerns be for identity matching?
Identity matching, if done incorrectly, may leak data of a person and create constant backdoor to their records. If matching is done in a very privacy preserving, non-linkable, non-traceable manner then catching the fact that something has at all happened may be hard, but also investigation on the topic would be hard.
Identity matching not done where needed leaves people without access to their records, for which they have legitimate rights to. This may hinder a person’s most basic functions such as health, ability to earn income or have access to their loved ones.
What will the future need for identity matching be and are the suggested solutions scalable?
EUDIW is identity matching machine – withing single EUDIW person is meant to generate as many pseudonyms as they wish, and service providers must accept these if law is not directly forcing people to reveal their actual personal data. Our solution does introduce EAA concept that is external proof of identities that can be matched, however given the nature of eIDAS and EUDIW ARF we do see that we are bound to have much more orphaned accounts to which the original owner will be unable to get access to even if they want to.
Suggestions on how quality of data across countries can be improved
Only used data is accurate and it is accurate because something depends on it. Therefore, link the data and use the linked data and show that to data subjects and make their life depend on it. We also believe that sharing the data about matches created will improve data quality and allow quicker error spotting.
eIDAS revision implications
At the point of report writing eIDAS revision still has not finished. However, the discussions and released versions of the text bring in several changes relevant to this report and we would like briefly to touch on the following:
- Electronic Attestation of Attributes. Electronic Attestation of Attributes is seen as Trust Service in regulation, and it will create greater clarity on organizational and technical requirements for such services and attestations themselves. However, nothing prohibits Nordic and Baltic countries to use such methods already now. In principle this is document with e-seal confirming that identity data set of one member state belongs to the same person as identity data set from another member state. These e-seals must be trusted by the NBCM community. As there is e-seal issuance and handling in current regulation then agreement can be made based on this. It is important to note that lifecycle management of such attestations must be well thought through. Although it is assumed that identity matching is done once and the link between identities is persistent forever, then as the process is open to errors of different kinds, the need to revoke this link must be foreseen. Attestation is a digital document and is living independently of its issuer. The other attestation related concern might be data privacy. Attestation should include only a minimal set of user data, but enough that it is unique to the member state it originates from. Additionally, it is possible to create attestations that would only be usable to validate the claim of identity matching and that cannot be used to derive the identities it connects. We do see that such discussions must take place before launching the system, but there are solutions that allow to implement a politically agreed solution.
- eID scheme notification obligation. eIDAS’ new version foresees that all member state will have to notify an identity scheme and at least one such scheme should be on the level of assurance high. Although this statement may change but it at least now gives hope that there is a way to authenticate from every member state using the highest level of assurance through eIDAS node infrastructure. There is no statement however how many citizens of any country such scheme should cover, but in our proposals, we can assume that for willing participant such mechanism is available, and it is not discriminatory to request using such scheme to interact with identity matching service.
- Introduction of EU Identity Wallet. The introduction of the EU Identity Wallet (EUDIW) will change the landscape of e-services in coming years and may well compete for attention and budget for most other issues either this report or any other may address. Therefore, alignment of this change has been a burning issue for the research. Introduction of EUDIW as mandatory tool for authentication for public and private sector services creates incentives to leave central identity brokers such as eIDAS Nodes infrastructure. We have therefore envisaged the EAA model alongside the eIDAS Node extension. We see that the proposal allows smooth transition from one model to another. However, we do see that the shift that is planned creates an environment without identity data that could be matched, rather a lot of pseudonyms and only claims about attributes existence. That leaves the active and cooperative participant sometimes without proper support - because data is not available to help then but even more it hides the traces of these who did not want to be matched in the first place. It leaves no room for state-to-state cooperation. So based on that we also feel that our focus on the scenario of helping a person who seeks help and is supportive on the identity matching is best suited.
3.4 Suggestions for Member States
We will now bring out country specific recommendations, that will ensure smooth implementation of our suggested solutions. General recommendations made by consultants have taken into account all the input gathered from every Nordic-Baltic country. Still, by mutual agreement, this report does not include recommendations concerning the identity matching solutions in Sweden, as their applicability would need a broader legal analysis, which was not within the scope of this study.
Denmark
Suggested solution: eIDASNode+
Reasoning: Denmark has identity matching solution in place, which aligns with eIDASNode+ principles. After piloting with manual process, Denmark has deployed automated process from October 2023.
Challenges/changes:
- Creation of new Danish identities during digital process of identity matching is not supported and requires longer term principal preparations in legal and organizational aspects. Currently creation of new identities requires physical presence in Denmark. In addition, feasibility of this change is questioned, because in practice persons requiring Danish personal identification number (CPR) are usually already residing in Denmark.
- Easy_EAA could be complimenting eIDASNode+, as in use cases of migration persons can have eID means of two countries at their hand.
- Retrieval of additional attributes besides eID 4 mandatory ones deemed to be necessary.
Faroe Islands
Suggested solution: eIDASNode+
Reasoning: Feasible approach from process and technical point of view.
Challenges/changes:
- No EU notified eID scheme and has not integrated with eIDAS node yet.
- Creation of new identity requires change in identity management ecosystem.
- Retrieval of additional attributes besides eID 4 mandatory ones deemed to be necessary.
Greenland
Suggested solution: eIDASNode+
Reasoning: Greenland has identity management setup following Denmark’s approach and is relying on Danish system.
Challenges/changes:
- Return on investment will have a very poor score due to the very limited number of transactions that might require identity matching.
Estonia
Suggested solution: eIDASNode+
Reasoning: Estonia is currently designing identity matching system, that aligns with eIDASNode+. Extending the solution with EAAs (Hard_EAA) is favorable. In addition, QuickFix could be deployed for subprocesses, where new identity is created.
Challenges/changes:
- Adjusting legal framework.
- Integration works of API between identity matching solution and e-services.
- Handling of identity matching results with lower level than ‘High’ in terms of LoA.
Finland
Suggested solution: eIDASNode+
Reasoning: Finland internal proposals for identity matching system are targeting same kind of solution.
Challenges/changes:
- Retrieval of additional attributes (e.g., citizenship, ID-document number) besides eID 4 mandatory ones deemed to be necessary.
- Changes in legislation and development of systems is necessary. In addition, topics needs prioritization for resources to be allocated.
- Handling of derived personal identity numbers increases identity matching complexity.
Latvia
Suggested solution: eIDASNode+
Reasoning: Technologically most suitable for deployment.
Challenges/changes:
- Retrieval of additional attributes (e.g., citizenship, ID-document number) besides eID 4 mandatory ones deemed to be necessary.
- Creation of new identity during identity matching process requires legislative changes.
- Conclude data exchange agreements with most countries’ population registries.
Lithuania
Suggested solution: eIDASNode+
Reasoning: Follows best established Lithuanian identity matching solution.
Challenges/changes:
- Accepting the identity matching results of other countries requires legislative and technological amendments.
- Levels of assurance for identity matching results require further analysis.
- e-services require significant time for adjustment to changes.
Norway
Suggested solution: eIDASNode+
Reasoning: Norway’s current outlook with identity matching solution aligns with principles of eIDASNode+.
Challenges/changes:
- Creation of identities for persons not residing in Norway requires changes in population registry.
- Appointing the owner of identity matching solution.
Iceland
Suggested solution: eIDASNode+
Reasoning: Technologically most suitable for deployment.
Challenges/changes:
- Legislation changes required.
- Creation of new identities during the identity matching process.
- e-services must adapt their business logic if matching results will have several levels of assurance, that do not align with currently established levels.